Securing your DNS - Android

Most people are not aware of this but by simply changing your DNS settings in your android device you can enhance your protection from malware.
It is extremely simple and does not require any major changes to your device or the installation of additional applications. What's more, it's free.
It does not however mean you are bullet proof
In this case I will use Cloudflare's DNS solution which is documented here.

So, in Network setting on your android devices, you simply setup private DNS, like so. You will now have additional protection against malware.
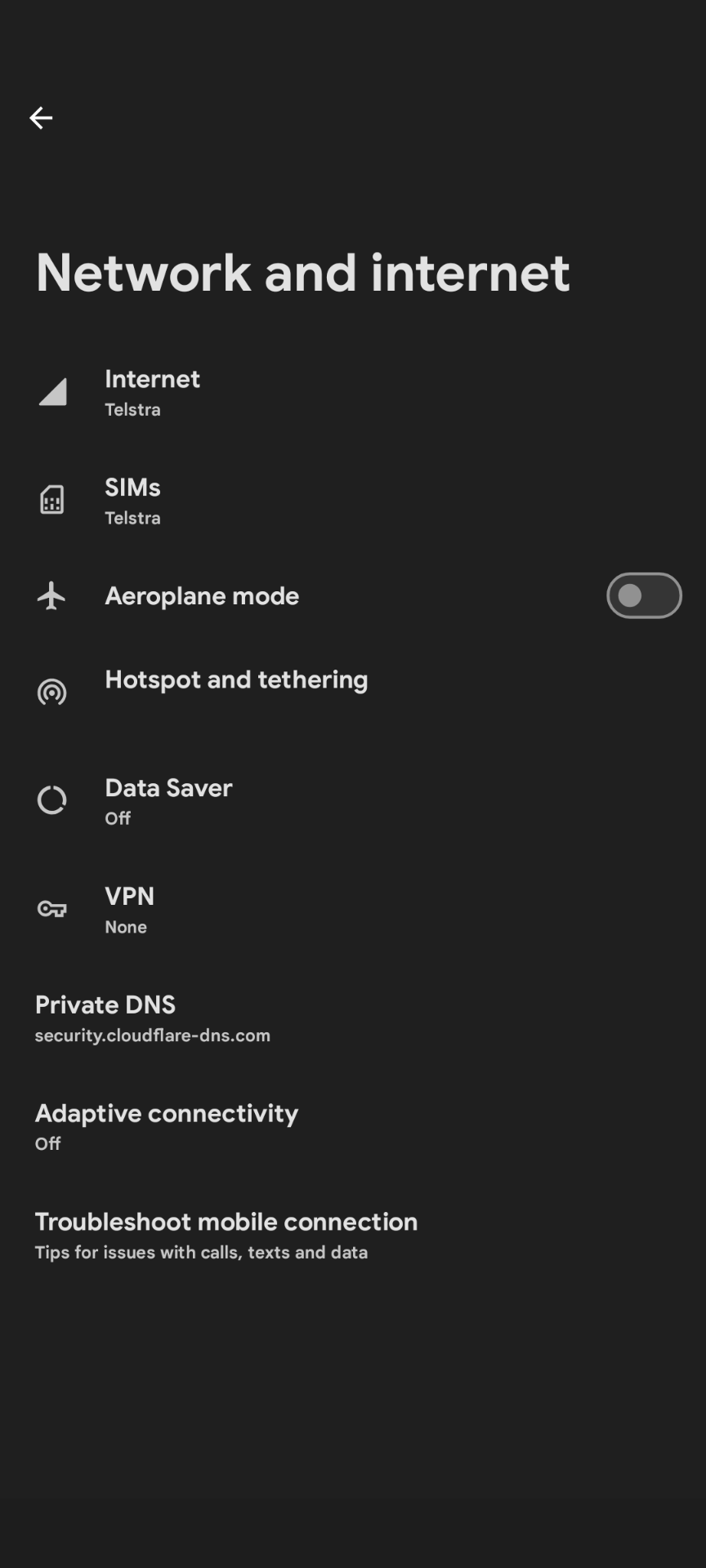
This will work when you're on the mobile network, and it will work when you're on Wi-Fi - yours or anyone else's. It will not work when using a VPN which by default uses their DNS resolvers - you will get a warning.
A few points. It will not stop malware getting on your device. It relies on DNS queries to Cloudflare to work. If the malware has hardcoded DNS, this won't work, yes - applications can have hardcoded DNS resolvers.
You can test it here, via your browser

Note that "Secure SNI" will probably fail, as it requires setting a flag in your favorite browser that is not available, although its browser independent.
Other operating systems. Yes, you can apply this to other devices either at the operating system level or just the browser. I would suggest the browser to start with.
There are extensive guides on how to do this on the internet.
A few years ago, I was subject to a DNS poisoning attack. This was about the time there was a massive campaign against VPN providers. I was not happy. It led me down the road of BGP, how it works, DNSSEC, and free so-called DNS providers. My conclusions at the time, were not to touch Googles DNS resolvers with a barge pole which is what led to the poisoning of my routers DNS cache. I still adhere to that conclusion.
I ended up with an ingress/egress firewall, bridging my router, changing my DNS and all things related to protecting my home, so it would never happen again.
Not all ISP's are created equally. I use our primary national provider and when I tested their BGP at the time, it failed. It has since passed. DNS is highly important to securing your network, a tier of defense and should not be taken lightly.
You can test your BGP here - if you are interested.

Leave you with it.
#enoughsaid


